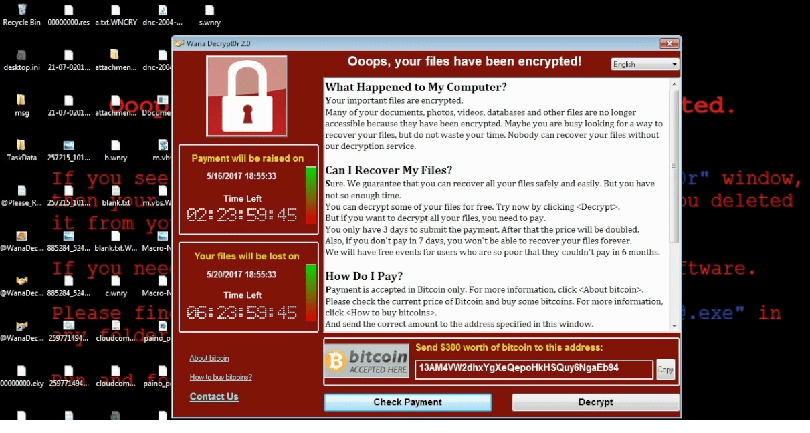
The WanaCrypt story so far: GIG’s Recommendations to Combat the Ransomware Threat
Authors: Navid Sobbi and Claude Khoury
WanaCrypt, WCry, WannaCry, WanaCryptor 2.0, and Wanna Decryptor Ransomware have all been covered by global media over the last 5 days. Unfortunately, much of the coverage has been lacking detailed analysis. We at NSI Global Counter Intelligence would like to do our part. We will shed light on this case and provide actionable content to help protect our readers.
The following article will systematically detail:
- What is WanaCrypt Ransomware?
- Speculation over the creators of WanaCrypt.
- The current extent of infection worldwide.
- Propagation: How does WanaCrypt spread?
- The specific vulnerability that has been exploited.
- How was the advance of WanaCrypt slowed?
- What is WanaCrypt 2.0?
- What specific measures to take before infection?
- What do I do if my system is infected?
- How to verify email attachments and links.
- About NSI.
What is WanaCrypt Ransomware?
Typical Ransomware uses one mechanism to infect. It usually spreads when people open emails containing infected links, or by opening attachments such as Word documents that are infected with malware. In the past, if you didn’t click on the infected link or attachment, the ransomware could not be installed.
There is a difference with WanaCrypt Ransomware though. WanaCrypt allows remote hacking to unpatched computers WITHOUT the users knowledge or involvement.
WanaCrypt has been designed to attack on TWO fronts:
- Firstly and most importantly, WanaCrypt exploits a vulnerability in unpatched Windows operating systems that allows remote access into your computer.
- Secondly, an encryptor is downloaded to the computer that has been infected and proceeds to encrypt all files.
Speculation over the creators of WanaCrypt.
Symantec Corp and Kaspersky Lab have identified similarities in the code used to create WanaCrypt and programs created by a North Korean hacking group known as Lazarus. Google threat intelligence researcher Neel Mehta was the first to identify the clue.
Lazarus are allegedly responsible for a string of cyber attacks including the high-profile Sony attack in the wake of the Seth Rogen and James Franco comedy The Interview and a string of attacks launched on banks in 18 countries last month.
The similarities could just be a case of one hacker copying and pasting another hackers code. It is also speculated this could even be a false flag left to mislead investigators.
However, the evidence is compelling enough to continue investigations following this lead.
“We believe this might hold the key to solve some of the mysteries around this attack. One thing is for sure — Neel Mehta’s discovery is the most significant clue to date regarding the origins of WanaCrypt” the researchers say.
The current extent of infection worldwide.
At the time of this writing, Europol has announced the infection has spread to:
| · A Spanish telecommunications company. | · More than 200,000 computers in approximately 150 countries. |
| · A dozen hospitals in England. | · The German rail network. |
| · The UK offices of Federal Express. | · The Russian Interior Ministry. |
| · Automobile Manufacturers Nissan and Renault. | · 12 Australian Businesses |
It is expected the spread of this attack will continue to grow in the coming days.
The specific vulnerability that has been exploited.
WanaCrypt is spread through a Windows vulnerability in the Server Message Block which allows remote access to the victim’s computer. The NSA discovered this vulnerability and created “EternalBlue”. This is the codename for their Trojan program.
Analysis seems to confirm that Friday’s attack was enabled using the suspected NSA code which was leaked by a group of hackers known as The Shadow Brokers. It used a variant of the Shadow Brokers’ EternalBlue Exploit (CC-1353). The creators of WanaCrypt used this information to take advantage of this exploit.
The vulnerability allows the EternalBlue Exploit (CC-1353) to scan for open ports on unpatched Windows computers. It looks at printer ports, serial ports, TCP ports such as port 445, etc. Once found, the first generation WanaCrypt requested a specific domain/URL that was created as a killswitch within the original EternalBlue Trojan. If it received a positive result, i.e. that the domain/URL existed, then it stops. If it gets a negative result, it will then install the encryptor.
The Shadow Brokers have since stated they will be releasing more zero-day exploits that will attack desktops and mobile devices (zero-day exploits refer to vulnerabilities in software that are unknown to the vendor). They will be launching a subscription-based model whereby members will get the latest leaks and hacks on a monthly basis.
Propagation: How does WanaCrypt spread?
Once the system is infected, it may infect an entire local area network, in the manner of a computer worm. The encryptor scans other computers on the network and attempts to find the same vulnerability to exploit. The encryptor encrypts files on a computer and then presents a window to the user with a ransom demand to decrypt them. It changes the file extensions on files to one of the following: .wnry, .wcry, .wncry and .wncrypt.
Then, the Trojan changes the desktop wallpaper to one that contains information about the infection and what actions the user needs to undertake to decrypt the files. The message will keep on displaying to ensure the user receives the message. When a system is infected, the user will need to pay a ransom in Bitcoins to decrypt the files. The ransom will increase every few hours/days. There is also no guarantee the files will be decrypted when the ransom is paid. Microsoft Windows actually created a patch for this vulnerability on the 14th of March, 2017, however, many people did not update their systems.
Patching your system will protect it from the exploit, however, it will not protect it from human error. That is, if a user unknowingly clicks on a link or opens an attachment in an email that was sent from an attacker. These can contain Trojan code which will then install the encryptor.
How was the advance of WanaCrypt slowed?
A researcher known as Malware Tech managed to suspend the malware by registering the domain name that was embedded within the Trojan code of the WanaCrypt. Once the domain was registered, it received thousands upon thousands of hits and thus saved those computers from becoming infected. This killswitch option may have been placed into the code by the creators in the event something went wrong.
This discovery however, allowed the creators to remove the killswitch and thus release WanaCrypt 2.0.
What is WanaCrypt 2.0?
WanaCrypt 2.0 is the latest killswitch free version of this Ransomware. The infection can no longer be stopped by the these means.
What measures to take before infection?
Microsoft has issued a statement stating that they will be adding detection and protection against the new malware known as Ransom:Win32.WannaCrypt
Those who are running the Windows free antivirus software and have Windows update enabled, are protected.
Some steps to put in place:
- Ensure you always update Windows
- Install a patch from Microsoft by going to this link.
- When scrolling down the page, find your operating system
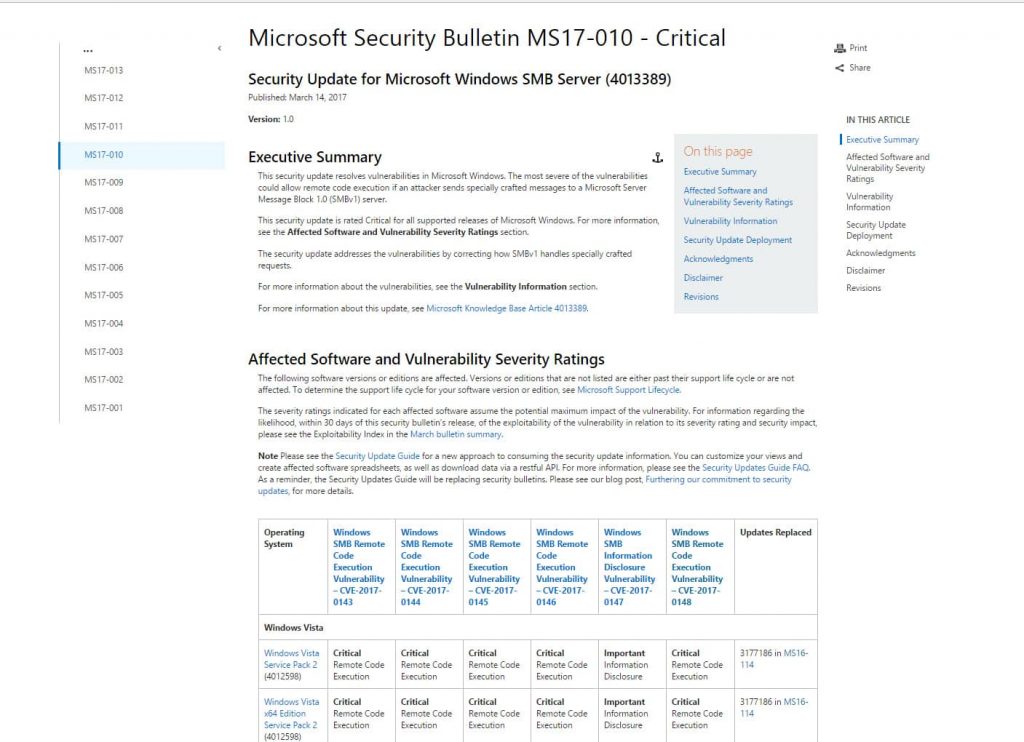
Once you find your operating system, select whether your system is a 32 bit or 64 bit system
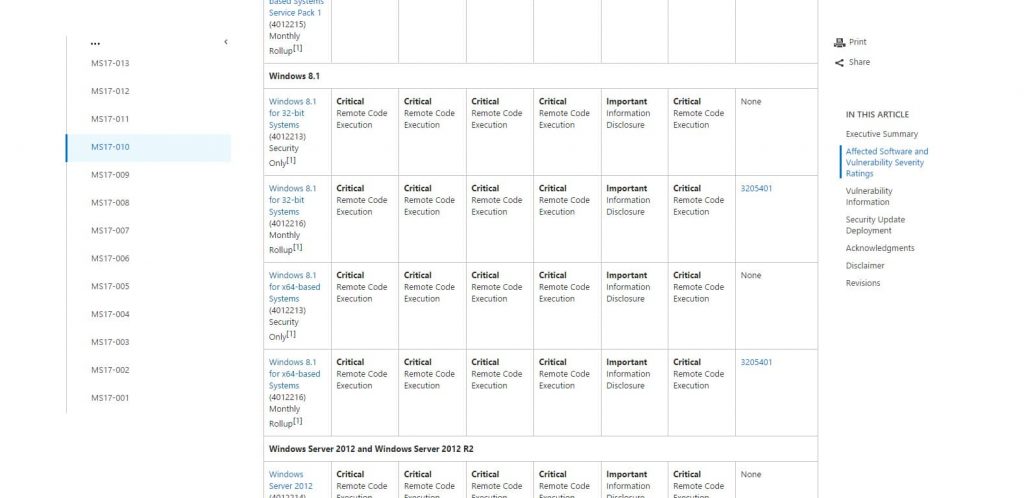
Click the corresponding x32 or x64 based system and wait for a new window to load. The new window will display the Microsoft Update Catalog. From here, you will need to click the download button that corresponds to your system (x32, or x64)
Testing
- This will begin the download. There is a high likelihood that you will need to use Internet Explorer to download this file. If the page displays an error, then there are steps that need to be taken to download this file.
- Ensure you have backed up your files and have a regular daily schedule for system backup. Critical files should be backed up on the fly.
- If you think you are vulnerable, you can disable the Server Message Block. This is an advanced process so you may need assistance from your IT team. Go to this link for instructions.
What do I do if my system is infected?
There is not much you are able to do. It is best not to pay the ransom. There have been reports of organisations having paid ransoms and still not getting their files decrypted. Ultimately the decision whether to pay the ransom or not is up to you.
How to verify email attachments and links.
To avoid infection, ensure that you never open an email that has an attachment or a link (especially from people that you know) without confirmation from the sender. Furthermore, it is best to confirm with the person that sent it verbally whenever possible. Additionally, a simple method to confirm if a link is not what it seems, is to hover over it with your mouse. Look at the link that is displayed at the bottom of the email or the web page. If it is a legitimate link it will display exactly what is displayed in the email.
If it is a spoofed link or a spam link you may notice that the URL differs from what is displayed in the email. It may look very similar; however, it may have a very slight difference from the original link. For example, instead of using the letter ‘O’ they may use the number ‘0’.
If the link displays any of these attributes DO NOT open it.
About Geopolitical Intelligence Group
GIG is an Australian owned Global Geopolitical Risk Advisory Firm. GIG has an interdisciplinary team of employees and partners in strategic locations around the globe.
Our Best in Class Services include:
| · Global Geopolitical Risk Advisory | · GIG Subscribe Intelligence |
| · Threat Intelligence | · Geopolitical Intelligence |
| · Strategic Global Intelligence | · Geopolitical Intelligence Advisory |
| · Global Insight |
GIG is called upon for its geopolitical intelligence expertise by corporations in the Mining, Oil and Gas industries, Financial Institutions, Insurance companies, Law and Accounting firms, Government agencies and High Net-Worth individuals. Our services are available globally with local offices in Sydney, Canberra, Abu Dhabi, Hong Kong and Singapore.
To book a confidential consultation. Feel free to contact our team.